
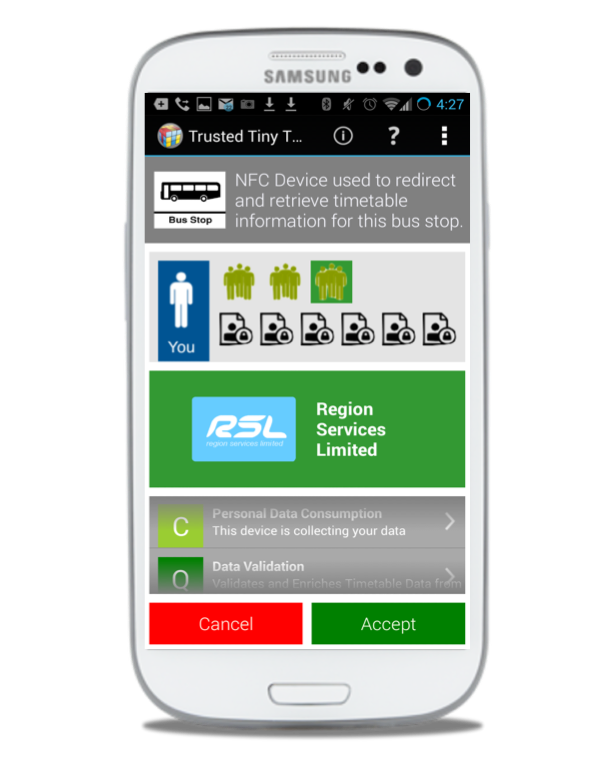
The vision of the Internet of Things (IoT) is a dynamic global network based on standard and interoperable communication protocols where physical and virtual ‘things’ have identities, physical attributes, and capabilities and are seamlessly integrated into the existing internet infrastructure [1]. The IoT is thus built upon a range of sensors and other devices that together represent the ‘things’; these devices range from passive radio tags to internet connected sensor platforms and embedded computers. Everyday deployments of such devices are increasingly commonplace. For example, passive NFC tags are currently in use by Aberdeenshire council to provide smartphone access to timetable information for a particular bus stop. Active IoT devices include vehicular telematics black boxes being introduced by insurance companies to assess the behaviour of drivers and affect their premiums. Such applications raise a number of issues, not least of which is the extent to which users understand these devices and their capabilities. Questions that a user might like to ask include: What kind of data does the thing collect? Is the data transmitted? If so, how and to whom? For what purposes are the data used? What control do I have over any aspects related to the generation and use of this data? Creating an infrastructure that would enable users to interrogate IoT devices to discover this (and other) information would, we argue, significantly increase trust in such devices and would provide reassurance to users (and society) as the roll-out of such technologies accelerates.
Our proposed solution is based upon additional metadata describing the context surrounding devices (e.g. manufacturer, owner, data transfer method). We argue that this can be provided by publishing information about devices according to the linked data principles [3]. As ‘things’ become more interconnected this context should also include provenance2 information: a record of the entities (devices or services) and processes (data transmission, data analysis, decision making) involved in the creation and use of data. A formal representation of provenance has been identified as essential to support users (and machines) to better understand and trust data [4]. For example, in the car black box scenario above, provenance could be used in order to understand what kind of data the box is collecting, what agents or services are using this data and for what purpose.
To create a lightweight model to represent information about devices in the IoT such as: capabilities, security properties, ownership and provenance of devices and services.
To develop an initial set of guidelines that could support IoT developers to describe information about devices according to our model.
To build a “Trusted Things” software framework based on Semantic Web technologies and services to store and query information about devices in the IoT and their associated provenance.
To evaluate this approach using a demonstrator application based on three scenarios: the use of passive NFC tags in bus shelters in Aberdeenshire; the use of in-car black boxes to track the behavior of drivers for insurance purposes and a smart toy.
This case study relates to the recent deployment of passive NFC tags by Aberdeenshire council to provide smartphone access to timetable information for bus stops. Passengers interested in obtaining real-time bus information can scan the NFC tag with a capable smartphone. The NFC tag embeds a URL containing a unique ID identifying the bus stop. This URL is used to redirect the smartphone web browser to a third party website displaying live timetable information. This scenario raises some questions regarding the privacy of the user. For example:
- What information are they collecting from my smartphone?
- Who is running the service?
- Are there any charges for the service?
- Where is the web browser re-directed?
- Would the service take contact-less payments?
(A feature normally associated with NFC technology).
The second case-study focuses on the use of in-car black boxes. Such boxes record information about driving style, location of the vehicle using a range of sensors including GPS and accelerometers. The information captured by the sensors is then transmitted to an insurance company typically via a 3G connection. This scenario also raises a number of questions regarding privacy. For example:
- What kind of data is being recorded?
- Who is using the data?
- When and where is the data transmitted?
- Is the data being sent to other third-party companies?
- For what purposes?
Cutting edge technology is now finding his way to childrens' toys. We are beginning to see toys loaded with sensors and capable of connecting to cloud services in order to make the toy more interactive. In this case study we are going to use
Hoot, a stuffed-toy barn owl instrumented with a Raspberry-pi, 3G connectivity and a number of sensors (GPS, camera, accelerometer, microphone, humidity and temperature)
This scenario raises some questions regarding the privacy and security of a child. For example:
- Can parents prevent the device from taking pictures or recording the voice of their child?
- Where is the data transmitted?
- What kind of data is being recorded?
- Who has access to the device?

is a Research Fellow working on trust and provenance issues in Linked Data at the dot.rural Digital Economy Hub. He has nine years experience in Semantic Web technologies, provenance and policy based reasoning gained during his involvement with a number of UK eScience projects. Since 2011 he has been involved (as a member) in activities related to the W3C provenance group which is currently working towards a standard language to support the widespread publication and use of provenance information of Web documents, data and resources.

is Professor of Computing Science at the University of Aberdeen, and has over 25 years experience in intelligent systems research. He is currently Director of the RCUK Digital Economy Hub 'dot.rural' and UK lead PI on the UK-India 'TRUMP' consortium, exploring the role of Semantic Web technologies in developing a trusted information architecture for quantified-self applications.

was awarded first class degree from University of Aberdeen in Computing Science. He is enthusiastic about socially entrepreneurial, ethical and professional topics in computing. He investigates how appropriate use of digital technologies can
improve well-being of society and how to further minimize impact of digital tools being used for wrongful purposes.
Stan is currently employed as a Research Assistant for Trusted Tiny Things project to support further developments in trust and transparency of IoT devices with respect to user privacy and user degree of control of such devices, so that IoT
Devices can become more secure and trustful by society.
Trusted Tiny Things: Making the Internet of Things More Transparent to Users
E. Pignotti & P.Edwards
Proceeding of ASPI '13: International Workshop on Adaptive Security, September 08 2013, Zurich, Switzerland.
doi:http://dx.doi.org/10.1145/2523501.2523503 (to appear)
Trusted Tiny Things
E. Pignotti & P.Edwards
DE2013: Open Digital Conference, 4 - 6 November, MediaCityUK, Salford.
Interrogating Capabilities of IoT Devices
S. Beran, E. Pignotti & P.Edwards
IPAW'14: Provenance Week, 9 - 13th June 2014, Cologne, Germany.





